Driven by the profits to be achieved via ransomware, most botnet operators have dropped banking Trojans in favor of supporting and running crypto-locking malware attacks, according to security experts who spoke Wednesday at cybersecurity firm Group-IB’s CyberCrimeCon 2020 virtual conference.
The volume of ransomware attacks continues to rise. Security experts say ransomware operators continue to innovate, lately including the creation of sites for naming-and-shaming victims and leaking or auctioning stolen data (see: Data-Exfiltrating Ransomware Gangs Pedal False Promises).
Cybercriminals have also been attempting to cash in on the COVID-19 pandemic. Since it began, “nothing really majorly changed in in terms of what cybercriminals were doing: They were still doing their phishing campaigns; they were still doing ransomware; they were still doing network intrusions,” said Craig Jones, director of cybercrime at Interpol, in a keynote presentation.
But Jones said attackers retooled many of those attacks to take advantage of the pandemic, which led to a rise in the number of remote workers, with many organizations having insufficient security controls to protect them all.
“We saw quite a spike in phishing emails,” he said. “We saw also malicious domains being set up in order to facilitate some of the criminal actions. We saw quite a difference as well in the ransomware, and I think maybe it might be because there was more reporting of it.”
Meanwhile, hospitals and other healthcare institutions have been subjected to a marked increase in ransomware attacks. The problem has been so acute that Interpol issued a purple notice to its 194 member countries. Unlike a red notice, which is an alert about the most wanted people around the world, “the purple notice is to alert law enforcement agencies to new MOs – new ways that the criminals are operating and taking advantage of communities at this vulnerable time,” Jones said.
Ransomware Operators Tap Affiliates
During the conference, Group-IB reviewed recent cybercrime trends and reported that ransomware gangs have been increasingly adopting affiliate programs. These involve ransomware operators building attack code and infrastructure, then recruiting affiliates to plant the malicious code on systems. Every time a victim pays, affiliate and operator share the profits (see: More Ransomware-as-a-Service Operations Seek Affiliates).
Dmitry Volkov, CTO of Group-IB, said affiliate-driven ransomware operations have also largely shifted their focus to larger targets, which tend to pay bigger ransoms. “This scheme became so popular that since the middle of 2019, the number of such affiliate programs doubled,” he said in a presentation at the conference.
Botnet Operators Drop Banking Trojans
Another measure of ransomware’s success is that the four largest banking botnets run by Russian speakers – Trickbot, Dridex, Qbot, and Silent Night – all shifted from banking malware to crypto-locking malware, Group-IB says.
Calculating the total damage caused by ransomware gangs is difficult. Based on known attacks, Group-IB says that 14 of the biggest ransomware gangs collectively shook down victims for at least $1 billion in ransom payments from the second half of 2019 through the first half of 2020.
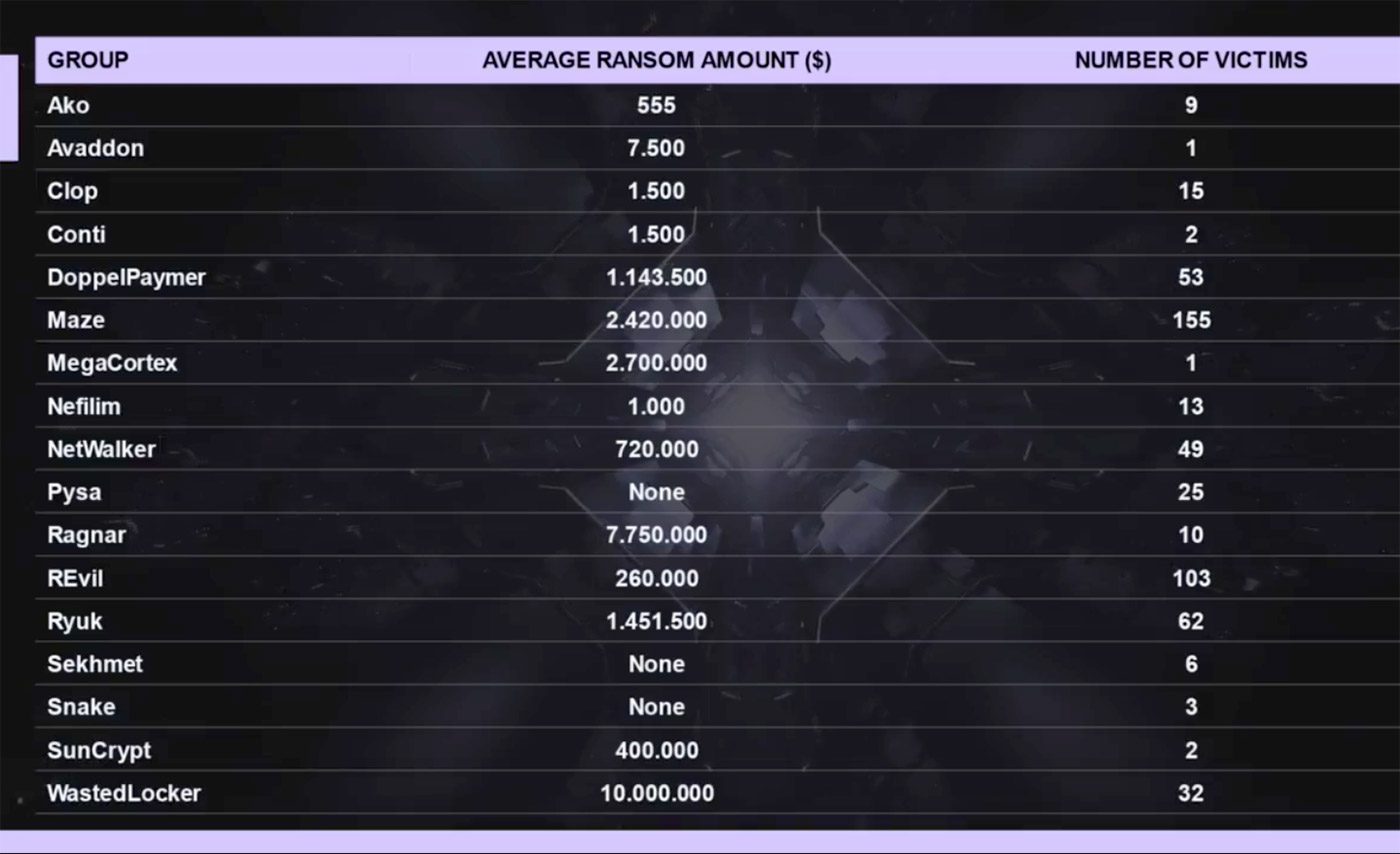
The average amount demanded by various ransomware gangs from the second half of 2019 through the first half of 2020 (Source: Group-IB)
The firm’s new Hi-Tech Crime Trends report covering that timeframe says there were more than 500 targeted ransomware attacks, half of which could be attributed to either the Maze gang and its affiliates, or to its rival Sodinokibi – aka REvil – ransomware-as-a-service program. The next most-active operations were Ryuk, NetWalker and DoppelPaymer, it says.
But only a fraction of ransomware attacks ever publicly come to light, meaning the actual profits being generated by ransomware could be significantly higher, Group-IB says. In the case of Ryuk, for example, “only 62 incidents involving Ryuk and spread using the banking Trojan Trickbot have been reported,” it says.
But the firm says its intelligence suggests that “the owners of the Trickbot botnet have successfully encrypted more than 2,500 different networks over the past year using ransomware such as Ryuk (later Conti), Kraken, and Thanos.” (See: Emotet, Ryuk, TrickBot: ‘Loader-Ransomware-Banker Trifecta’)
Rise of the Initial Access Brokers
Fueling the growth in ransomware attacks has been a marked increase in offerings from initial access brokers, which often run brute-force remote desktop protocol attacks to steal credentials that they sell to other criminals.
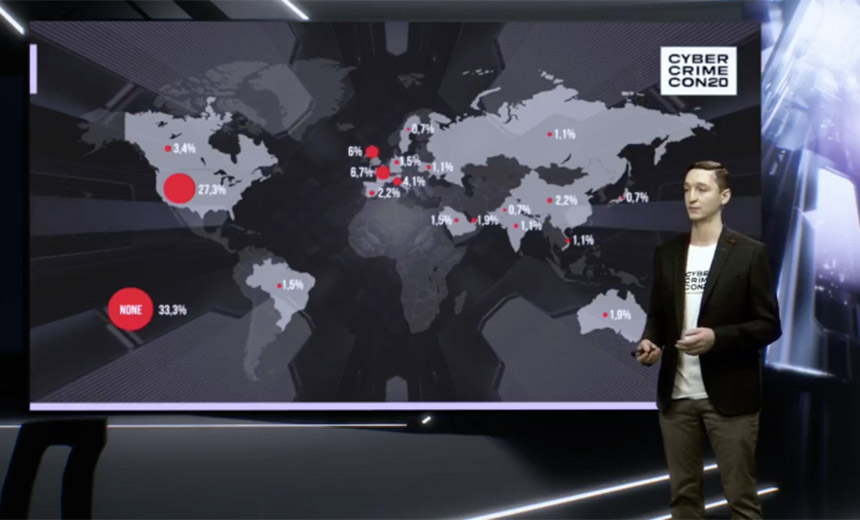
Initial access brokers are selling remote access to U.S. networks more than any other, Dmitry Volkov, CTO of Group-IB, said at CyberCrimeCon 2020
Group-IB says the sum of all prices for access information being offered by initial access brokers was about $1.6 million in 2018 and involved about 37 active sellers. By the first half of this year, the cumulative total had risen to $6.2 million, with 63 active sellers, of which 52 had only begun selling access credentials this year.
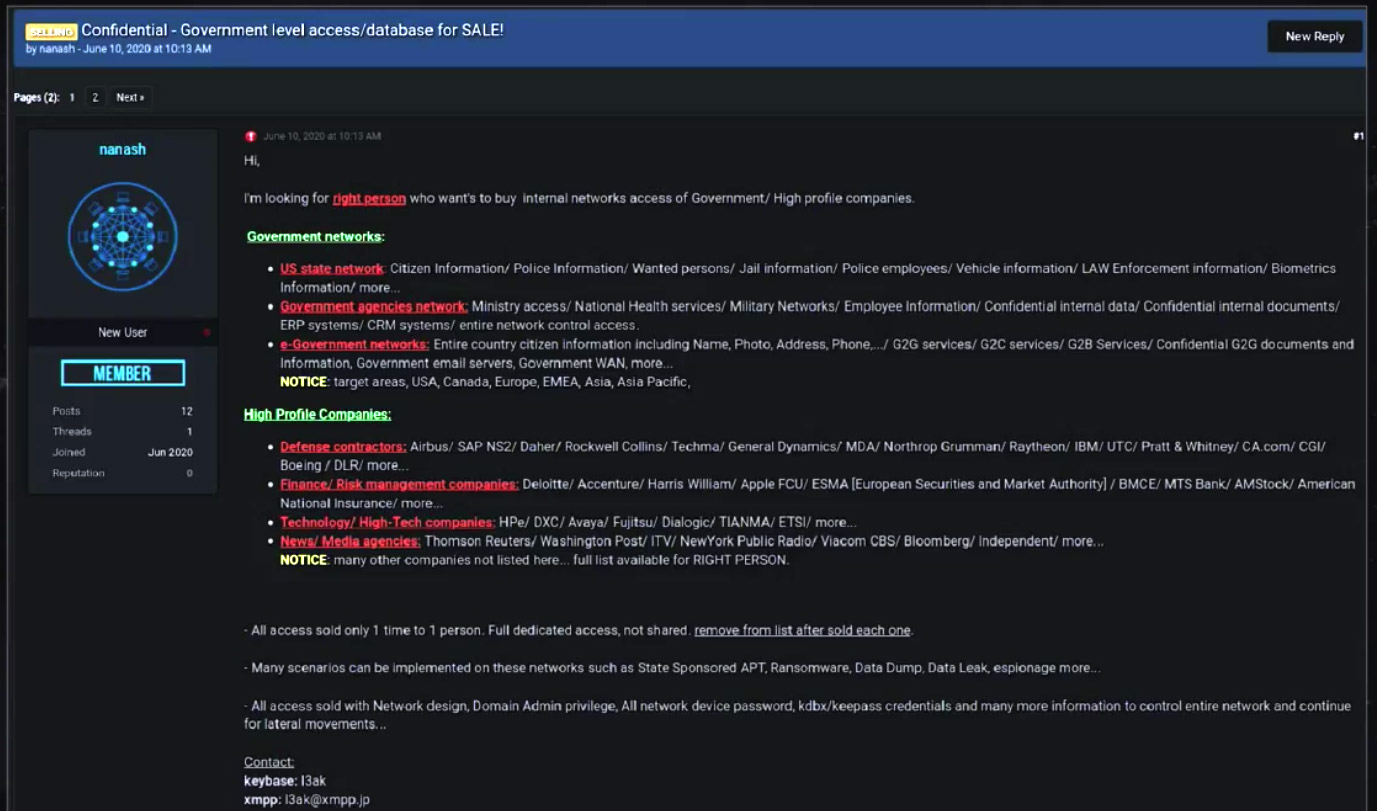
Cybercrime forum advertisement posted in June by an initial access broker offering access to government networks and “high-profile companies” (Source: Group-IB; click to enlarge)
The single greatest price demanded for remote access was 11 bitcoins – at the time of that advertisement, worth about $125,000 – although the price for access credentials can vary widely by the seller and the size of the victim organization, Volkov said.
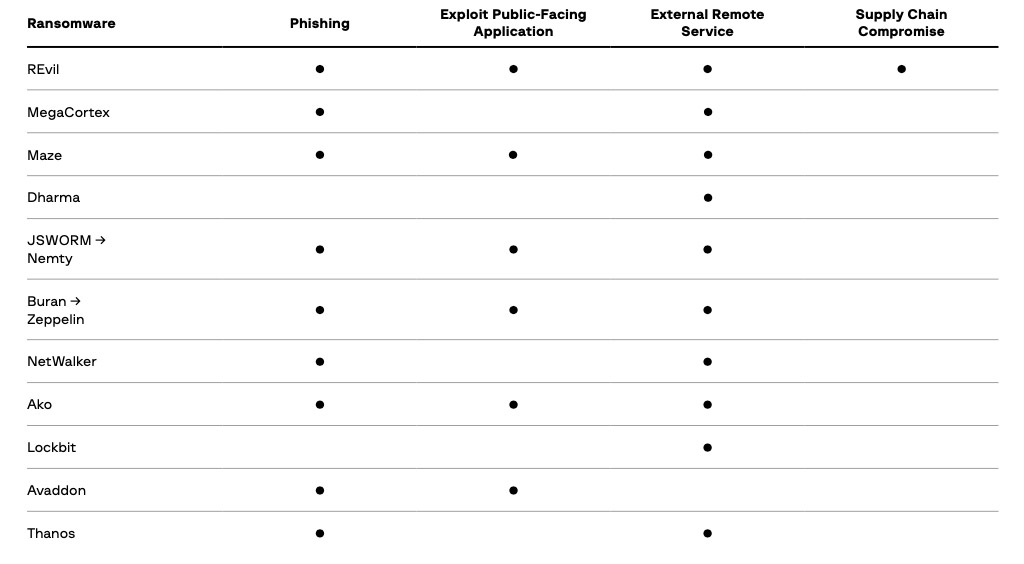
Here’s a list of initial compromise vectors for ransomware gangs with affiliate programs. “Most often, the initial intrusion vector was a malicious email campaign, a brute-force attack against remote desktop protocol or the exploitation of public-facing applications, including VPN-related,” Group-IB says.
For several years now, criminals have been continuing to exploit many of the same vectors: weak or poorly secured remote desktop protocol environments, using phishing campaigns to socially engineer victims, or gaining remote access by exploiting well-known flaws that victims have yet to patch, the security firm found.





























You must be logged in to post a comment Login