The Aberebot Android banking trojan has returned under the name ‘Escobar’ with new features, including stealing Google Authenticator multi-factor authentication codes.
The new features in the latest Aberebot version also include taking control of the infected Android devices using VNC, recording audio, and taking photos, while also expanding the set of targeted apps for credential theft.
The main goal of the trojan is to steal enough information to allow the threat actors to take over victims’ bank accounts, siphon available balances, and perform unauthorized transactions.
Rebranded as Escobar
Using KELA‘s cyber-intelligence DARKBEAST platform, BleepingComputer found a forum post on a Russian-speaking hacking forum from February 2022 where the Aberebot developer promotes their new version under the name ‘Escobar Bot Android Banking Trojan.’
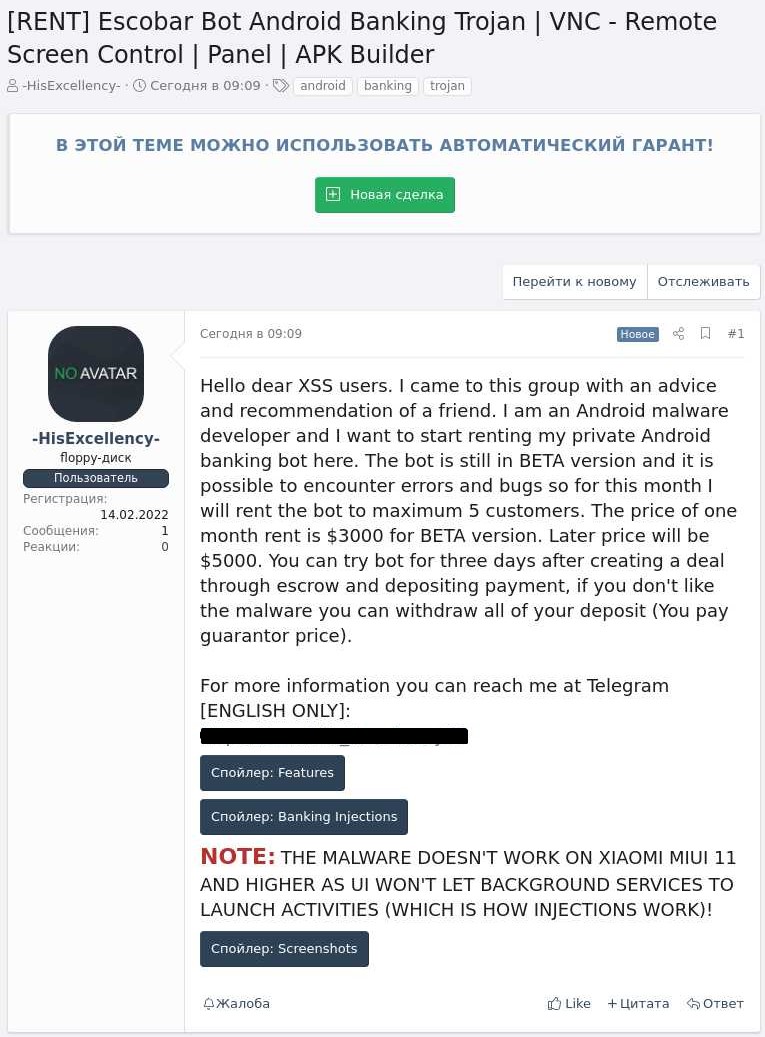
The malware author is renting the beta version of the malware for $3,000 per month to a maximum of five customers, with threat actors having the ability to test the bot for free for three days.
The threat actor plans on raising the malware’s price to $5,000 after development is finished.
MalwareHunterTeam first spotted the suspicious APK on March 3, 2022, masqueraded as a McAfee app, and warned about its stealthiness against the vast majority of anti-virus engines.
This was picked up by researchers at Cyble, who performed an analysis of the new ‘Escobar’ variant of the Aberebot trojan.
According to the same analysts, Aberebot first appeared in the wild in the summer of 2021, so the appearance of a new version indicates active development.
Old and new capabilities
Like most banking trojans, Escobar displays overlay login forms to hijack user interactions with e-banking apps and websites and steal credentials from victims.
The malware also packs several other features that make it potent against any Android version, even if the overlay injections are blocked in some manner.
The authors have expanded the set of targeted banks and financial institutions to a whopping 190 entities from 18 countries in the latest version.
The malware requests 25 permissions, of which 15 are abused for malicious purposes. Examples include accessibility, audio record, read SMS, read/ write storage, get account list, disabling the keylock, making calls, and accessing precise device location.
Everything that the malware collects is uploaded to the C2 server, including SMS call logs, key logs, notifications, and Google Authenticator codes.
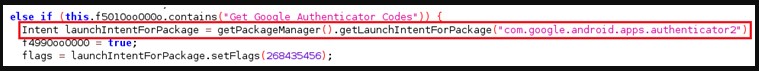
The above is enough to help the crooks overcome two-factor authentication obstacles when assuming control of e-banking accounts.
2FA codes arrive via SMS or are stored and rotated in HMAC software-based tools like Google’s Authenticator. The latter is considered safer due to not being susceptible to SIM swap attacks, but it’s still not protected from malware infiltrating the userspace.
Moreover, the addition of VNC Viewer, a cross-platform screen sharing utility with remote control features, gives the threat actors a new powerful weapon to do whatever they want when the device is unattended.
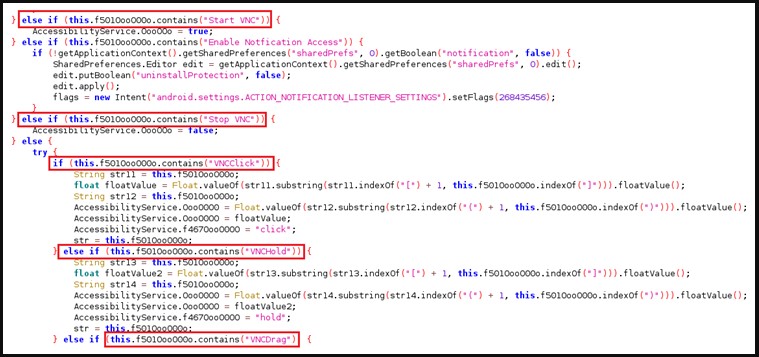
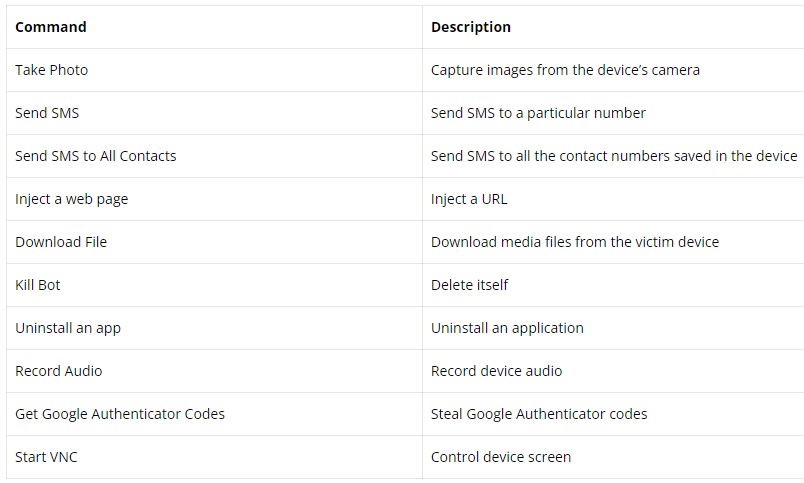
Apart from the above, Aberebot can also record audio clips or take screenshots and exfiltrate both to the actor-controlled C2, with the complete list of supported commands listed below.
Should we be concerned?
It is still early to tell how popular the new Escobar malware will become in the cybercrime community, especially at a relatively high price. Nevertheless, it’s now powerful enough to entice a wider audience.
Also, its operational model, which involves random actors that can rent it, means its distribution channels and methods may vary greatly.
In general, you can minimize the chances of being infected with Android trojans by avoiding the installation of APKs outside of Google Play, using a mobile security tool, and ensuring that Google Play Protect is enabled on your device.
Additionally, when installing a new app from any source, pay attention to unusual requests for permissions and monitor the app’s battery and network consumption stats for the first few days to identify any suspicious patterns.






























You must be logged in to post a comment Login