Security analysts have uncovered a recent phishing campaign from Russian hackers known as APT29 (Cozy Bear or Nobelium) targeting diplomats and government entities.
The APT29 is a state-sponsored actor that focuses on cyberespionage and has been active since at least 2014. Its targeting scope is determined by current Russian geopolitical strategic interests.
In a new campaign spotted by threat analysts at Mandiant, APT29 is targeting diplomats and various government agencies through multiple phishing campaigns.
The messages pretend to carry important policy updates and originate from legitimate email addresses belonging to embassies.
.png)
Another notable aspect in this campaign is the abuse of Atlassian Trello, and other legitimate cloud service platforms, for command and control (C2) communication.
Phishing campaign details
The spear-phishing campaign started in January 2022 and continued through March 2022 in several waves that rotated to various topics and relied on multiple sender addresses.
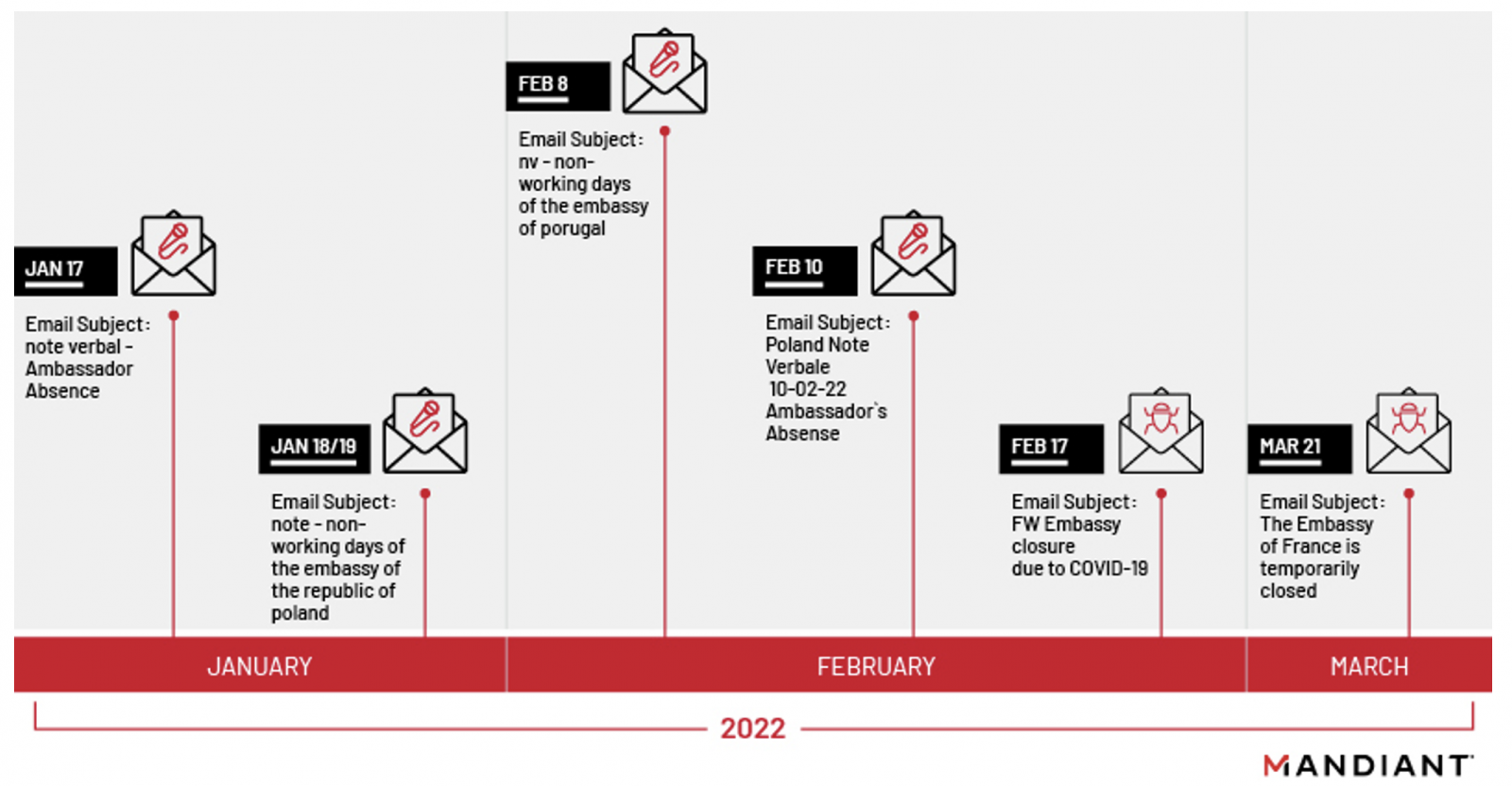
In all cases, the phishing emails originated from a legitimate compromised email address belonging to a diplomat, so recipients would be more trusting in the content delivered this way.
Mandiant found that the initially compromised addresses were listed as contact points on embassy websites.
The email used the HTML smuggling technique to deliver an IMG or ISO file to the recipient, a technique that APT29 has used numerous times in the past with great success, including in the SolarWinds attacks.
The ISO archive contains a Windows shortcut file (LNK) that executed an embedded malicious DLL file when clicked.
To trick the victim into clicking, the LNK file pretends to be a document file with the real extension hidden and a fake icon.
Malware drop
The DLL execution results in the delivery of the BEATDROP downloader, which runs in memory after creating a suspended thread to inject itself into, and connects to Trello for C2 communication.
Trello is widely used in corporate environments, so using its API for malicious network traffic is unlikely to raise any critical flags from security products.
In later efforts, APT29 replaced BEATDROP with a new C++ BEACON loader based on Cobalt Strike that features higher-level capabilities.
These capabilities include keylogging, taking screenshot, a proxy server mode, account credentials exfiltration, enumeration, and port scanning.
Both loaders deployed BOOMIC, which Microsoft tracks as VaporRage, discovered and analyzed in May 2021. In many cases, BOOMIC was side-loaded mere minutes after the loader was deployed.
BOOMIC establishes persistence by modifying the Windows registry and then downloads various obfuscated shellcode payloads and runs them in memory.
Mandiant observed various legitimate compromised websites serving as BOOMIC’s C2, which helps avoid URL blocklisting problems.
.png)
Lateral movement
After establishing a presence in an environment, APT29 escalates privileges in less than 12 hours, using various methods like writing files that contain Kerberos tickets.
Next, they perform extensive network reconnaissance to identify valid pivoting points and snatch more valuable passwords, and finally, move laterally by dropping more Cobalt Strike beacons and then BOOMIC on adjacent systems.
“Analysis of SharedReality.dll identified it to be a memory-only dropper written in Go language that decrypts and executes an embedded BEACON payload. The BEACON payload was identified to be SMB BEACON that communicates over the SharedReality.dll Named Pipe,” Mandiant says.
“APT29 was then observed utilizing the impersonation of a privileged user to copy SharedReality.dll to the Temp directory of multiple systems. The group then deployed it via a scheduled task named SharedRealitySvcDLC, which was installed and executed. After executing the scheduled task, the task was then immediately deleted” – Mandiant
No matter the persistent and tight tracking of APT29 by competent threat intelligence teams, the group remains a top-level espionage threat for high-interest targets.






























You must be logged in to post a comment Login