Extended spellcheck features in Google Chrome and Microsoft Edge web browsers transmit form data, including personally identifiable information (PII) and in some cases, passwords, to Google and Microsoft respectively.
While this may be a known and intended feature of these web browsers, it does raise concerns about what happens to the data after transmission and how safe the practice might be, particularly when it comes to password fields.
Both Chrome and Edge ship with basic spellcheckers enabled. But, features like Chrome’s Enhanced Spellcheck or Microsoft Editor when manually enabled by the user, exhibit this potential privacy risk.
Spell-jacking: That’s your spellcheck sending PII to Big Tech
When using major web browsers like Chrome and Edge, your form data is transmitted to Google and Microsoft, respectively, should enhanced spellcheck features be enabled.
Depending on the website you visit, the form data may itself include PII—including but not limited to Social Security Numbers (SSNs)/Social Insurance Numbers (SINs), name, address, email, date of birth (DOB), contact information, bank and payment information, and so on.
Josh Summitt, co-founder & CTO of JavaScript security firm otto-js discovered this issue while testing his company’s script behaviors detection.
In cases where Chrome Enhanced Spellcheck or Edge’s Microsoft Editor (spellchecker) were enabled, “basically anything” entered in form fields of these browsers was transmitted to Google and Microsoft.
“Furthermore, if you click on ‘show password,’ the enhanced spellcheck even sends your password, essentially Spell-Jacking your data,” explains otto-js in a blog post.
“Some of the largest websites in the world have exposure to sending Google and Microsoft sensitive user PII, including username, email, and passwords, when users are logging in or filling out forms. An even more significant concern for companies is the exposure this presents to the company’s enterprise credentials to internal assets like databases and cloud infrastructure.”
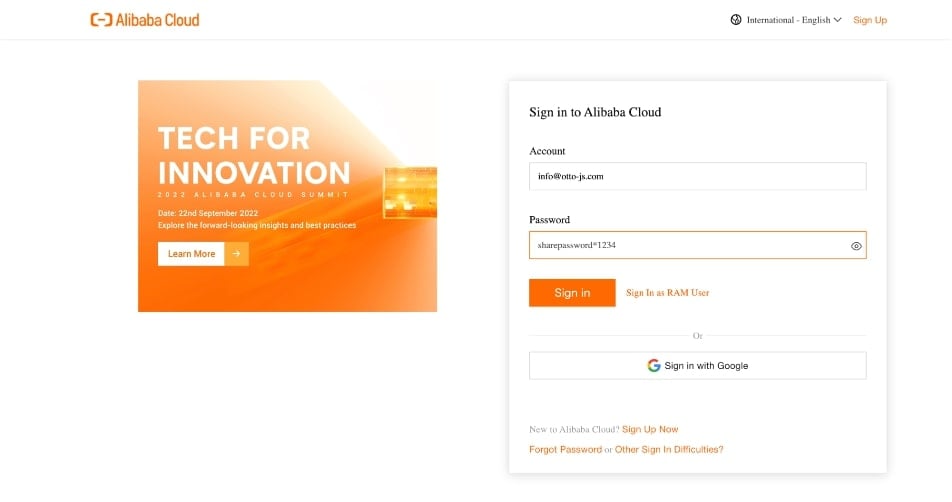
Users may often rely on the “show password” option on sites where copying-pasting passwords is not allowed, for example, or when they suspect they’ve mistyped it.
To demonstrate, otto-js shared the example of a user entering credentials on Alibaba’ Cloud platform in the Chrome web browser—although any website can be used for this demonstration.
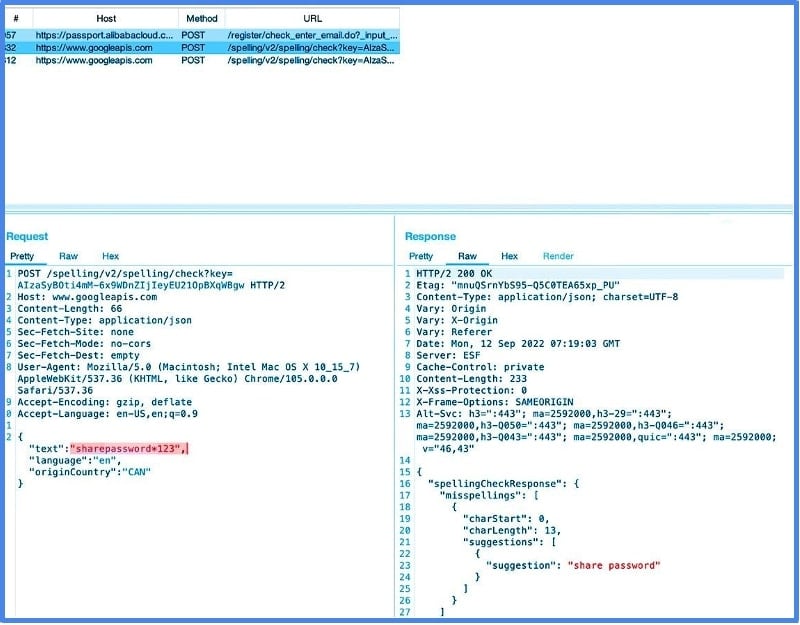
With enhanced spellcheck enabled, and assuming the user tapped “show password” feature, form fields including username and password are transmitted to Google at googleapis.com.
A video demonstration has also been shared by the company:
BleepingComputer also observed credentials being transmitted to Google in our tests using Chrome to visit major sites like:
- CNN—both username and password when using ‘show password’
- Facebook.com—both username and password when using ‘show password’
- SSA.gov (Social Security Login)—username field only
- Bank of America—username field only
- Verizon—username field only
A simple HTML solution: ‘spellcheck=false’
Although the transmission of form fields is happening securely over HTTPS, it may not be imminently clear as to what happens to user data once it reaches the third-party, in this example, Google’s server.
“The Enhanced spell check feature requires an opt-in from the user,” a Google spokesperson confirmed to BleepingComputer. Note, that this is in contrast to the basic spellchecker that is enabled in Chrome by default and does not transmit data to Google.
To review if Enhanced spell check is enabled in your Chrome browser, copy-paste the following link in your address bar. You can then choose to turn it on or off:
chrome://settings/?search=Enhanced+Spell+Check
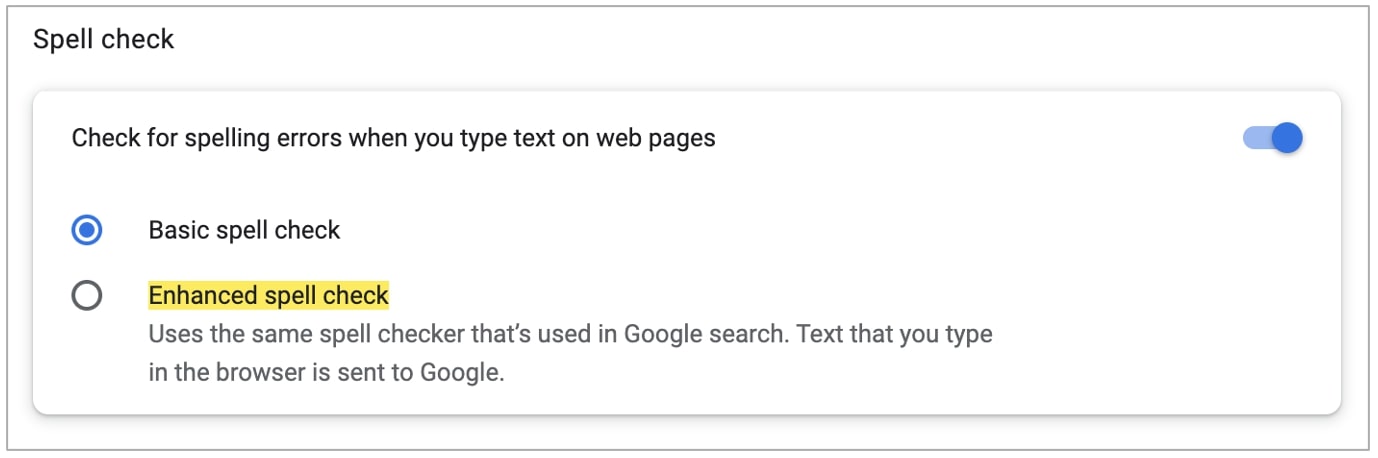
As evident from the screenshot, the feature’s description explicitly states that with Enhanced spell check enabled, “text that you type in the browser is sent to Google.”
“The text typed by the user may be sensitive personal information and Google does not attach it to any user identity and only processes it on the server temporarily. To further ensure user privacy, we will be working to exclude passwords proactively from spell check,” continued Google in its statement shared with us.
“We appreciate the collaboration with the security community, and we are always looking for ways to better protect user privacy and sensitive information.”
As for Edge, Microsoft Editor Spelling & Grammar Checker is a browser addon that needs to be explicitly installed for this behavior to take place.
BleepingComputer reached out to Microsoft well in advance prior to publishing. We were told that the matter was being looked into but we are yet to hear back.
otto-js dubbed the attack vector “Spell-jacking” and expressed concern for users of cloud services like Office 365, Alibaba Cloud, Google Cloud – Secret Manager, Amazon AWS – Secrets Manager, and LastPass.
Reacting to otto-js’ report, both AWS and LastPass mitigated the issue. In LastPass’ case, the remedy was reached by adding a simple HTML attribute spellcheck=”false” to the password field:
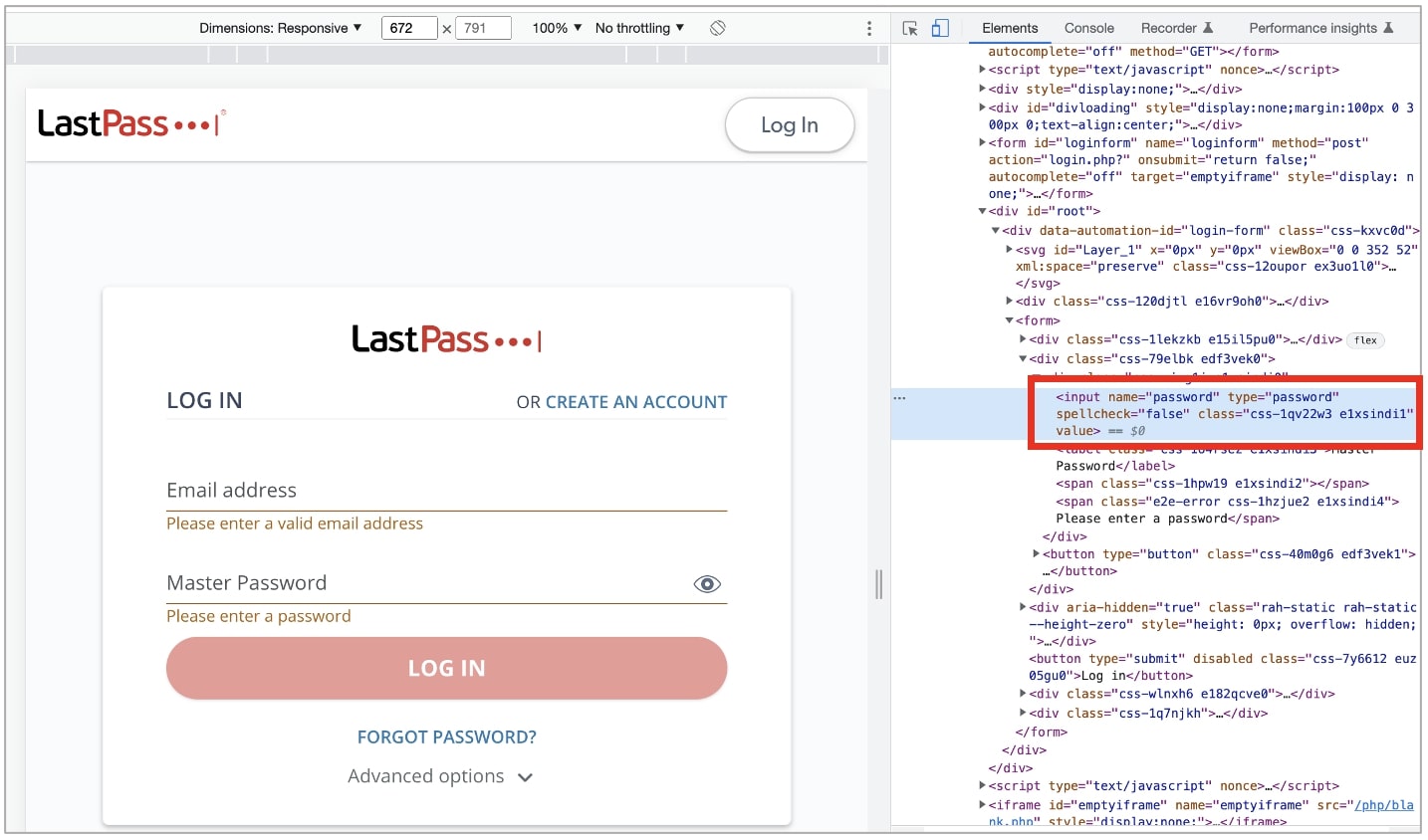
The ‘spellcheck’ HTML attribute when left out from form text input fields is usually assumed by web browsers be true by default. An input field with ‘spellcheck’ explicitly set to false will not be processed through a web browser’s spellchecker.
“Companies can mitigate the risk of sharing their customers’ PII – by adding ‘spellcheck=false’ to all input fields, though this could create problems for users,” explains otto-js referring to the fact, users will now no longer be able to run their entered text though spellchecker.
“Alternatively, you could add it to just the form fields with sensitive data. Companies can also remove the ability to ‘show password.’ That won’t prevent spell-jacking, but it will prevent user passwords from being sent.”
Ironically enough, we observed Twitter’s login form, which comes with the “show password” option, has the password field’s “spellcheck” HTML attribute explicitly set to true:
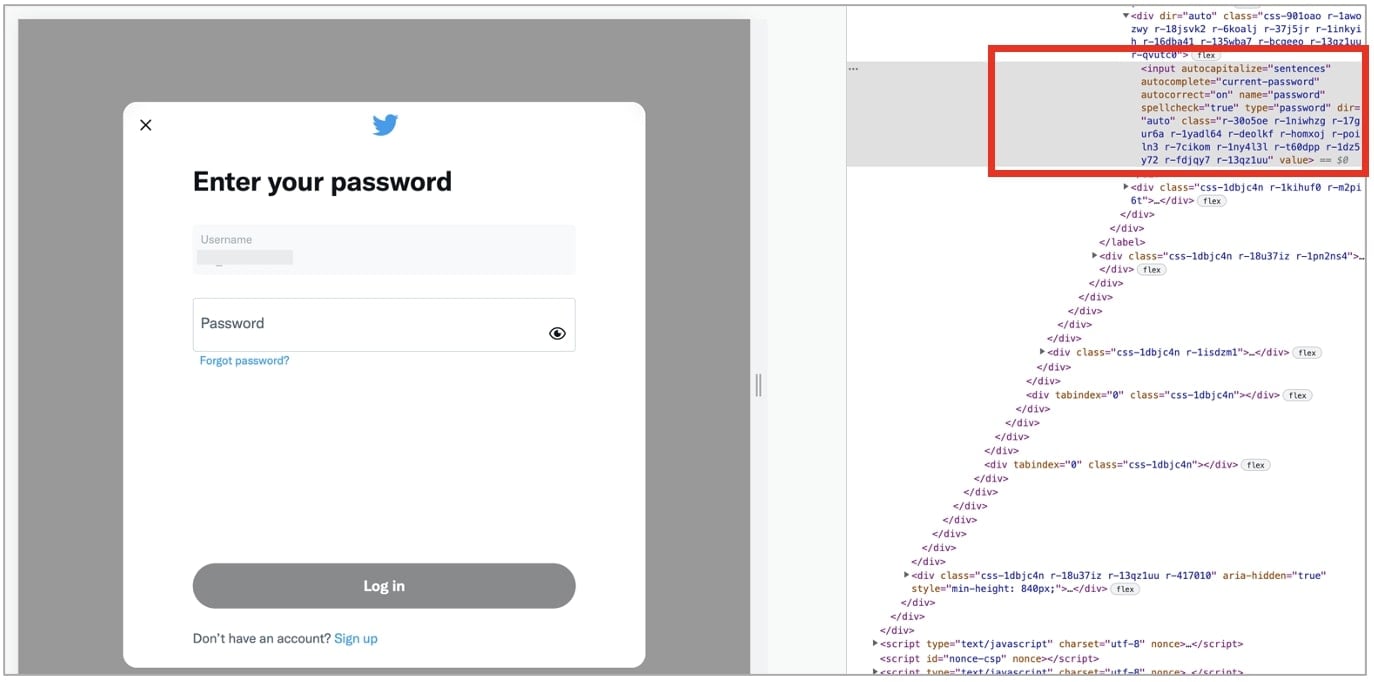
As an added safeguard, Chrome and Edge users can turn off Enhanced Spell Check (by following the aforementioned steps) or remove the Microsoft Editor add-on from Edge until both companies have revised extended spellcheckers to exclude processing of sensitive fields, like passwords.






























You must be logged in to post a comment Login