The North Korean Lazarus hacking group is now using fake ‘Crypto.com’ job offers to hack developers and artists in the crypto space, likely with a long-term goal of stealing digital assets and cryptocurrency.
Crypto.com is one of the world’s leading cryptocurrency exchange platforms. The company gained attention in 2021 when it purchased and rebranded the Los Angeles Staples Center arena into ‘Crypto.com Arena’ and began a series of TV advertisements promoting the service.
The Lazarus hacking group has been running a campaign dubbed ‘Operation In(ter)ception’ since 2020, where they target people working in the cryptocurrency industry.
The threat actors’ goal is to trick targets into opening malicious files that infect systems with malware that can be used to breach the internal networks of crypto companies to steal large amounts of cryptocurrency, NFTs, or conduct espionage.
In August 2022, Lazarus was seen targeting IT workers with malicious job offers that impersonated Coinbase and targeted users with Windows malware or macOS malware.
In a new report by Sentinel One, the hackers have now switched to impersonating Crypto.com in their phishing attacks using the same macOS malware seen in previous campaigns.
Latest campaign details
Lazarus typically approaches their targets via LinkedIn, sending them a direct message to inform them of a lucrative job opening in a large company.
Like the previous macOS campaigns, the hackers sent a macOS binary posing as a PDF containing a 26-page PDF file named ‘Crypto.com_Job_Opportunities_2022_confidential.pdf’ that contains alleged job vacancies at Crypto.com.
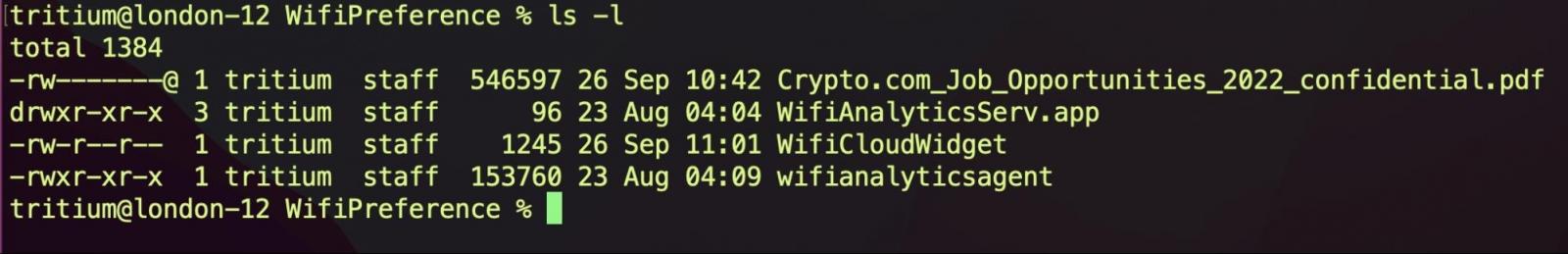
In the background, the Mach-O binary creates a folder (“WifiPreference”) in the user’s Library directory and drops the second and third-stage files.
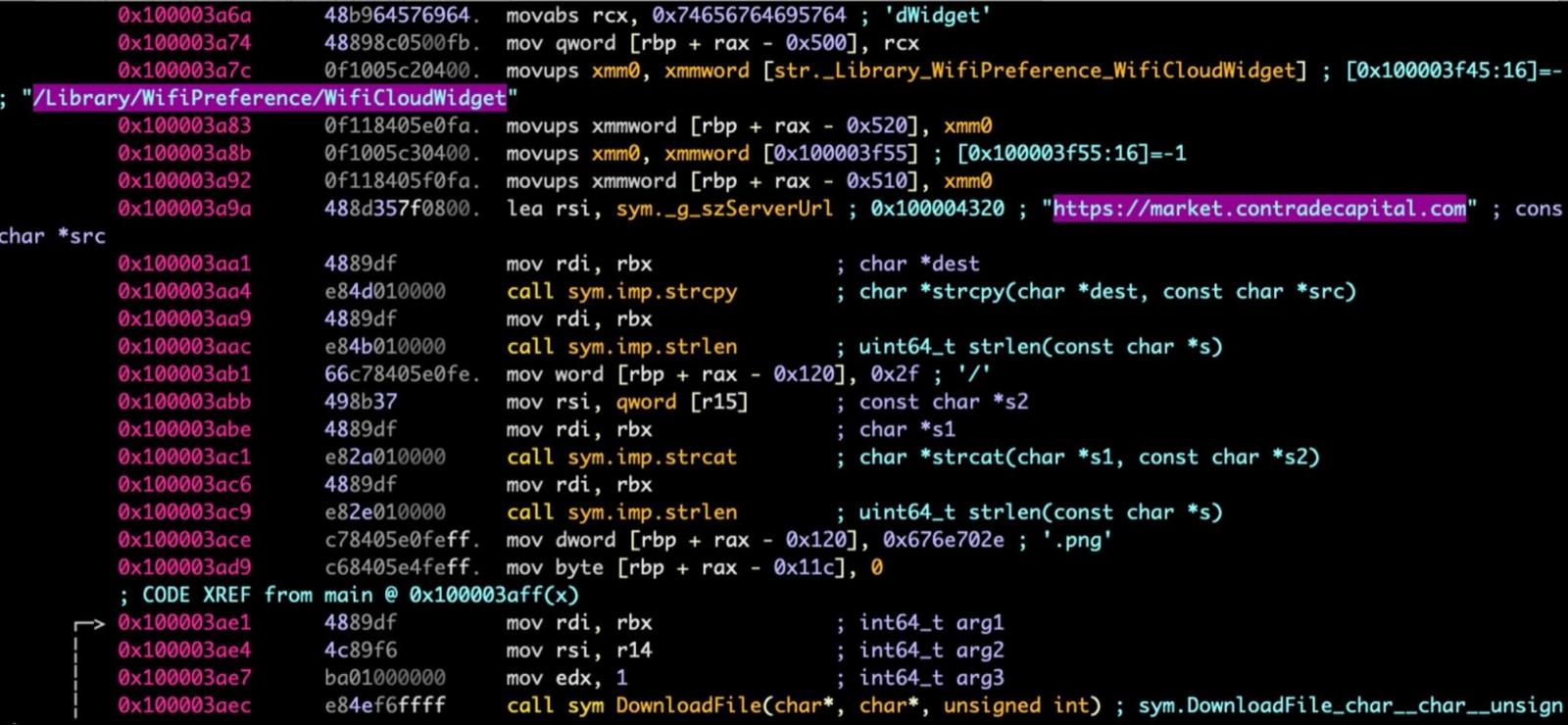
The second stage is “WifiAnalyticsServ.app” that loads a persistence agent (“wifianalyticsagent”), which eventually connects to the C2 server at “market.contradecapital[.]com” to fetch the final payload, “WiFiCloudWidget.”
The security researchers couldn’t retrieve the final payload for analysis due to the C2 being offline at the time of the investigation.
However, they noticed characteristics that point to a short-lived operation, which is typical for ‘Operation In(ter) ception’ campaigns.
“The threat actors have made no effort to encrypt or obfuscate any of the binaries, possibly indicating short-term campaigns and/or little fear of detection by their targets,” explains Sentinel One in their report.
The binaries are signed with an ad hoc signature, so they can pass Apple Gatekeeper checks and execute as trusted softwar
.jpg)
Likely, Lazarus will soon switch to impersonating a different company while keeping the rest of the attack elements largely unmodified.
If you work on a crypto firm, be vigilant with unsolicited job offers on LinkedIn, as one moment of curiosity is enough to act as a trojan horse for your employer.
Crypto firms are a popular target for Lazarus
Cryptocurrency firms are a popular target for the Lazarus North Korean state-sponsored hacking group, which is believed to be responsible for the theft of over $600 million in cryptocurrency.
Lazarus first targeted cryptocurrency users by spreading trojanized cryptocurrency wallets and trading apps that steal people’s private keys and drain their holdings.
In April, the U.S. Treasury and the FBI linked the Lazarus group to a cyberattack that stole over $617 million worth of Ethereum and USDC tokens from blockchain-based game Axie Infinity.
It was later revealed that the Axie Infinity hack was made possible due to a laced PDF file that contained a lucrative job offer sent to one of the blockchain’s engineers.






























You must be logged in to post a comment Login