A malicious for-profit group named ‘Fangxiao’ has created a massive network of over 42,000 web domains that impersonate well-known brands to redirect users to sites promoting adware apps, dating sites, or ‘free’ giveaways.
The imposter domains are used as part of what appears to be a massive traffic generation scheme that creates ad revenue for Fangxiao’s own sites or more visitors for ‘customers’ who purchase traffic from the group.
According to a detailed report by Cyjax, the threat actors are based out of China. They have been operating since 2017, spoofing over 400 renowned brands from the retail, banking, travel, pharmaceuticals, transport, financial, and energy sector.
Examples given in the report include Coca-Cola, McDonald’s, Knorr, Unilever, Shopee, Emirates, and more, with many fake sites featuring extensive localization options.
Often, Fangxiao victims are redirected to sites that infect them with the Triada trojan or other malware. However, a connection between the operators of these sites and Fangxiao has yet to be established.
Profit factory
To generate massive traffic for its customers and its own sites, Fangxiao registers approximately 300 new brand impersonation domains daily.
Since the start of March 2022, the malicious operators have used at least 24,000 landing and survey domains to promote their fake prizes to victims.
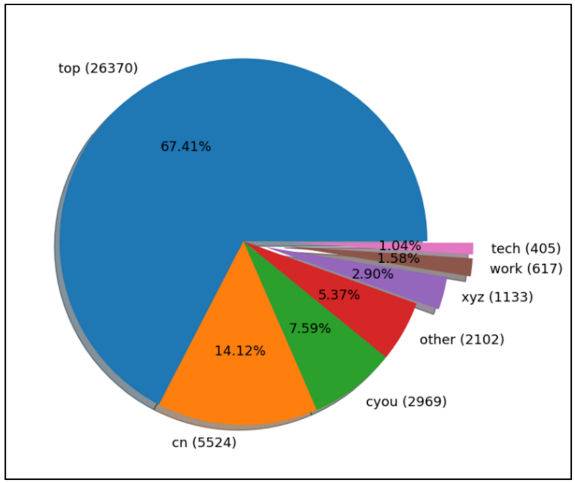
Most of these sites use the “.top” TLD, followed by “.cn”, “.cyou”, “.xyz”, “.work”, and “.tech”. The sites are hidden behind Cloudflare and registered through GoDaddy, Namecheap, and Wix.
Users arrive on these sites through mobile advertisements or after receiving a WhatsApp message containing the link, typically making a special offer or informing the recipient they won something.
These landing domains redirect visitors to a survey domain with a timer that adds urgency to help keep the victims concentrated away from the signs of fraud.
.png)
In some cases, completing the survey leads to downloading an app, which the victim is requested to launch and keep open for at least thirty seconds, likely to allow enough time to register a new user from a Fangxiao referral.
The landing sites also host advertisements from ylliX, which Google and Facebook have marked as “suspicious” while clicking on them results in a separate redirection chain.
The redirection path depends on the user’s location (IP address) and user agent, leading to Triada trojan downloads, Amazon via affiliate links, fake dating sites, and SMS micropayment scams.
Another observed destination of the Fangxiao campaign is the Play Store page of the ‘App Booster Lite – RAM Booster’ app, a performance booster for Android devices with over 10 million downloads.
Cyjax says the app does not feature malicious functionality, but it asks users to approve access to risky permissions, and it serves above average amount of ads through hard-to-close popups.
The app’s publisher, LocoMind, shares an IP address with another app developer named Holacode, who has been previously linked to adware distribution.
A full list of domains found by Cyjax to be used in this campaign can be found here.
Conclusion
Cyjax’s investigation yielded several indications that Fangxiao is a Chinese operator, like using Mandarin on one of the exposed controlled panels.
However, apart from some email addresses linked to hacking forums like OGUsers, there are no further clues about the identity of the threat actors.
Also, it is currently unknown if this massive baiting operation using many fake sites to draw victims is related to the final destinations or if Fangxiao is merely collaborating with those sites to make a profit.
Copyright 2021 Associated Press. All rights reserved.






























You must be logged in to post a comment Login