Attackers abused open redirects on the websites of Snapchat and American Express in a series of phishing attacks to steal Microsoft 365 credentials.
Open redirects are web app weaknesses that allow threat actors to use the domains of trusted organizations and websites as temporary landing pages to simplify phishing attacks.
They’re used in attacks to redirect targets to malicious sites that will either infect them with malware or trick them into handing over sensitive information (e.g., credentials, financial info, personal info).
“Since the first domain name in the manipulated link is in fact the original site’s, the link may appear safe to the casual observer,” email security firm Inky, which observed the attacks, explained.
“The trusted domain (e.g., American Express, Snapchat) acts as a temporary landing page before the surfer is redirected to a malicious site.”
Abused to target thousands of potential victims
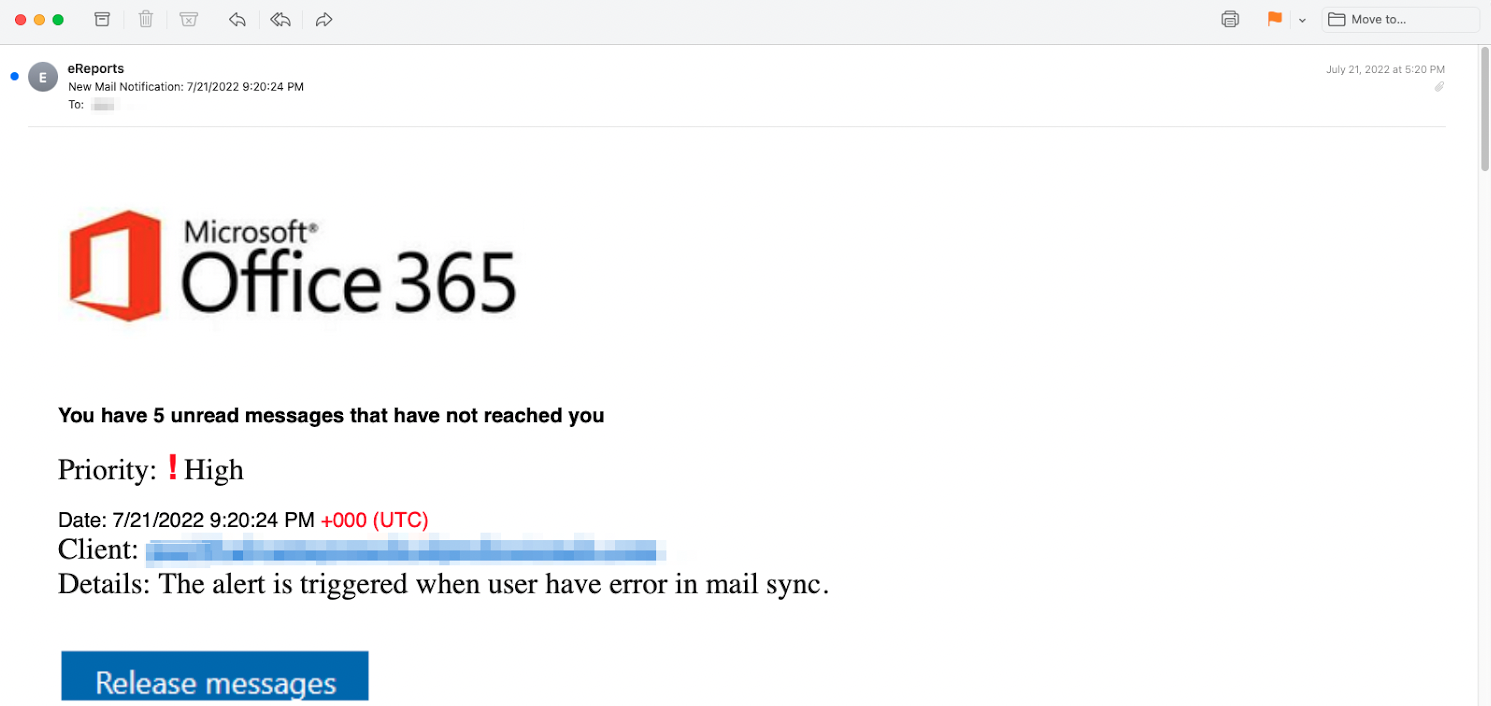
According to Inky researchers, the Snapchat open redirect was used in 6,812 phishing emails sent from Google Workspace and Microsoft 365 hijacked over two and a half months.
These emails impersonated Microsoft, DocuSign, and FedEx and redirected the recipients to landing pages designed to harvest Microsoft credentials.
While the Snapchat vulnerability was reported to the company through the Open Bug Bounty platform one year ago, on August 4, 2021, the open redirect is yet to be patched.
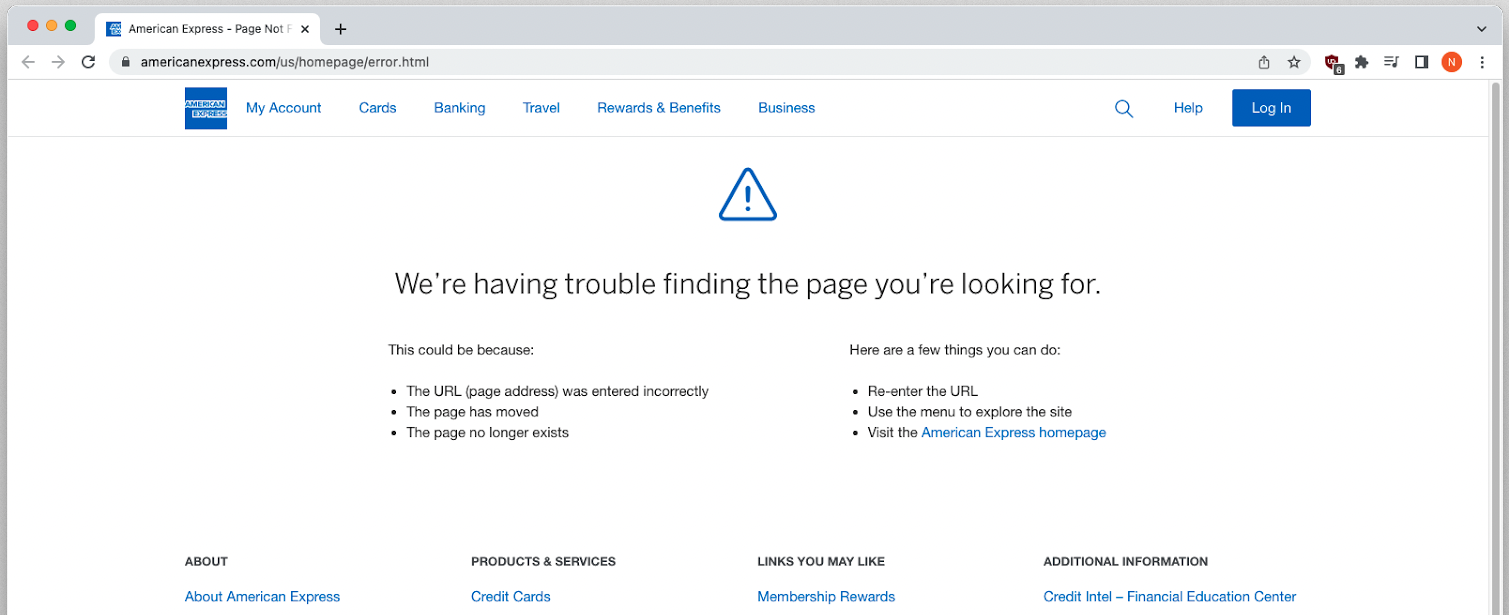
On the other hand, the American Express open redirect was quickly patched after being exploited for a couple of days during late July. New attempts to abuse it now land on an American Express error page.0
Before being addressed, the Amex open redirect was used in 2,029 phishing emails using Microsoft Office 365 baits, sent from recently registered domains and designed to funnel potential victims to Microsoft credential harvesting sites.
“In both the Snapchat and the American Express exploits, the black hats inserted personally identifiable information (PII) into the URL so that the malicious landing pages could be customized on the fly for the individual victims,” Inky explained.
“And in both, this insertion was disguised by converting it to Base 64 to make it look like a bunch of random characters.”
To defend against such attacks, Inky advised email recipients to check for “url=,” “redirect=,” “external-link,” or “proxy” strings or multiple occurrences of “HTTP” in URLs embedded in emails likely showing an indication of redirection.
Website owners are also recommended to implement external redirection disclaimers that request users to click before being redirected to external sites.